Nokia portfolio of industrial applications and devices
Select based on your needs/requirements
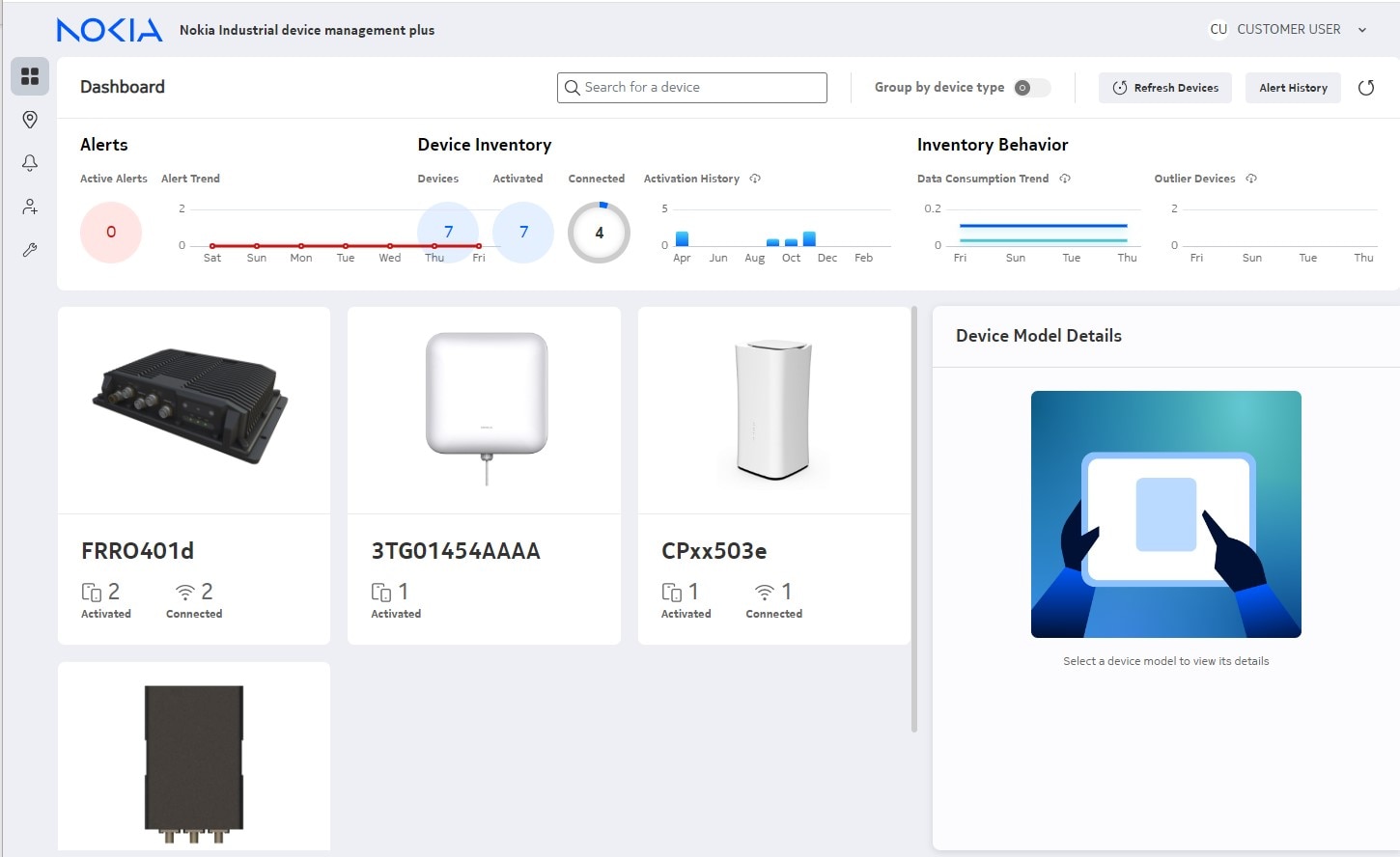
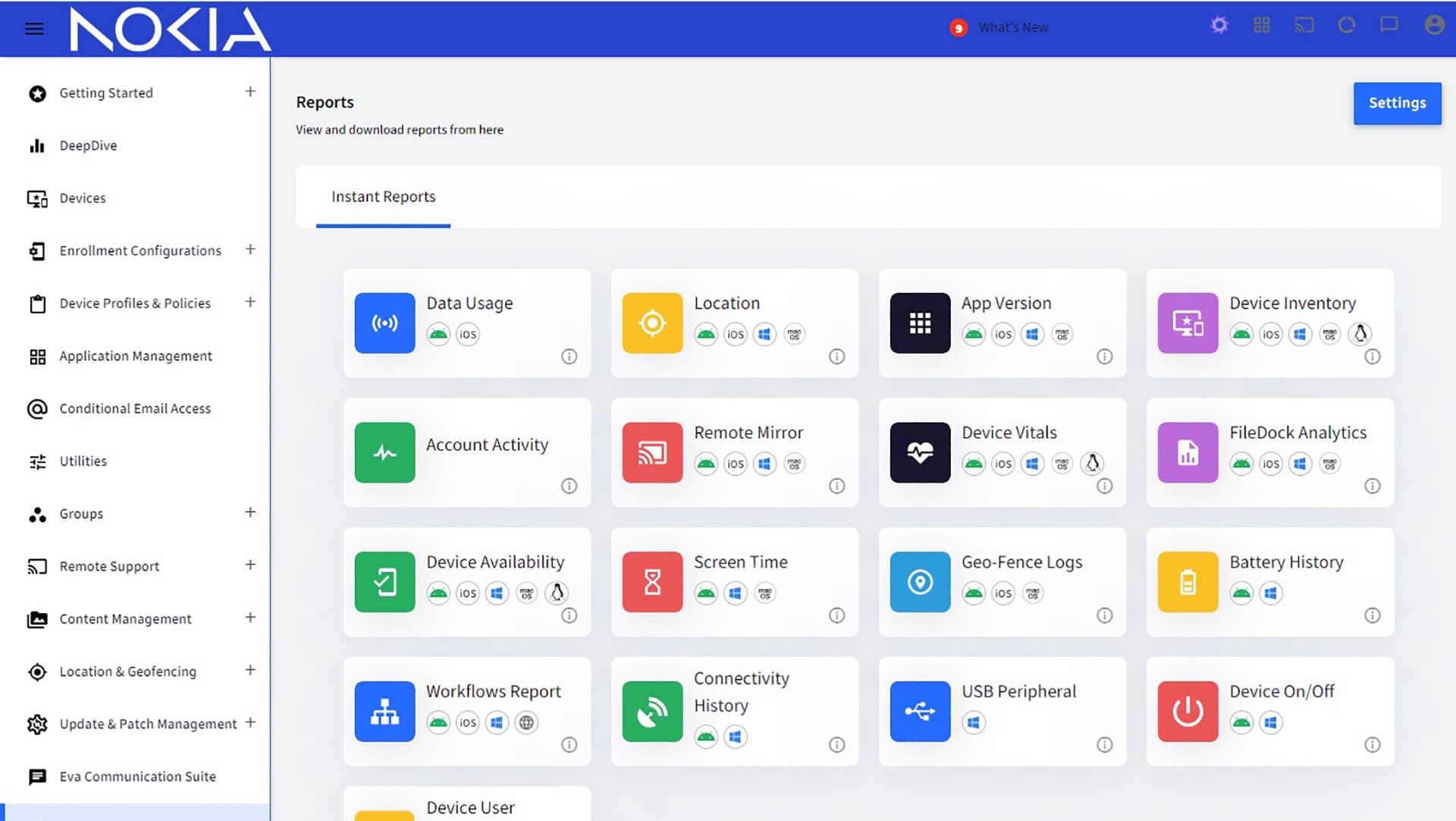
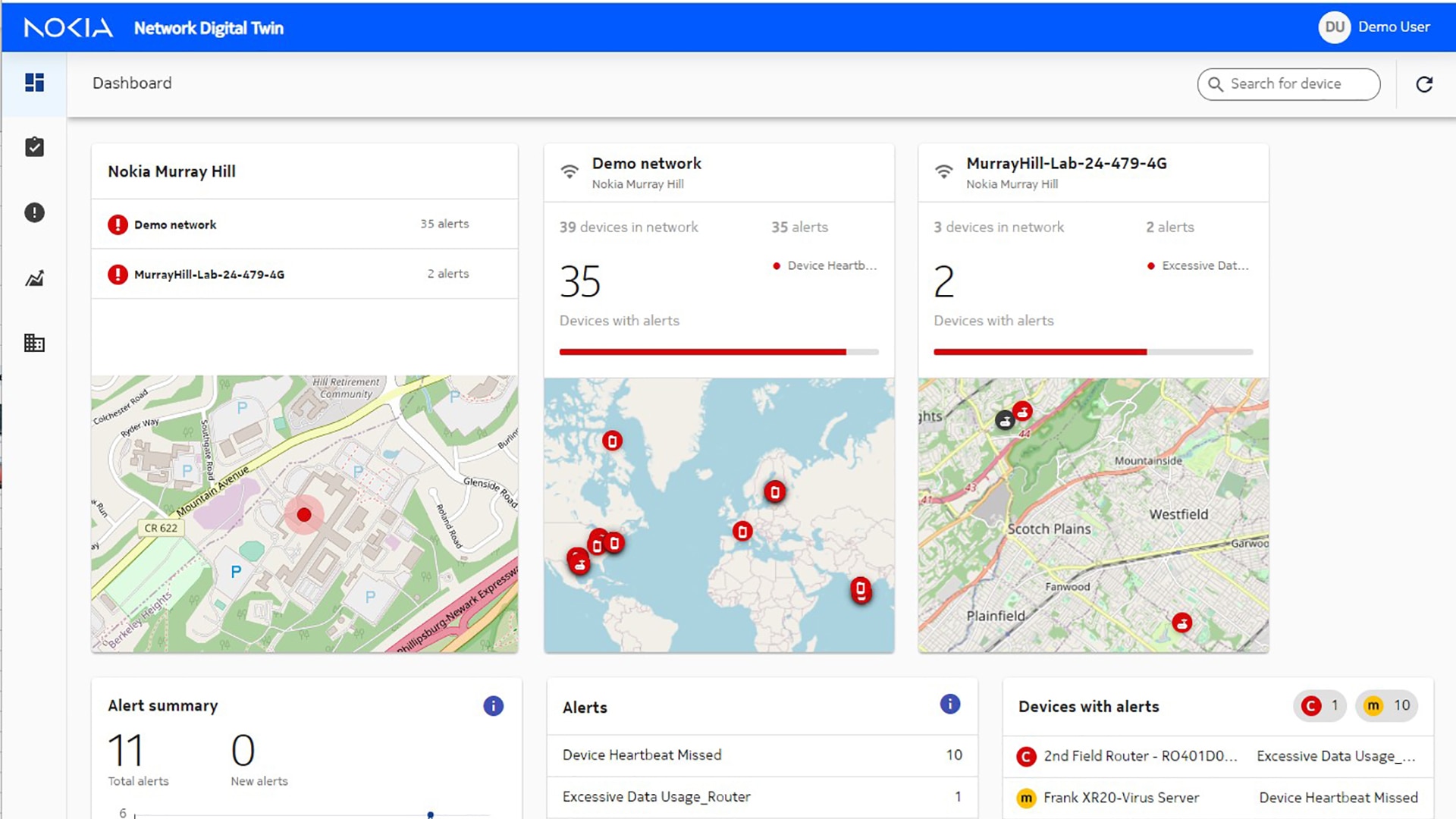
Featured applications and devices
Featured applications
Featured Devices
Portfolio
Product types
Application types
Device categories
Industrial use cases
- Anomaly detection
- Asset management
- Connected workers and assets
- Digital library
- Digital twin
- Emergency response
- Energy management
- Machine automation
- Physical access control gate
- Quality inspection
- Remote experts
- Remote machine control
- Robotic and mechatronic automation
- Site security
- Situational awareness
- Surveillance
- Tracking and positioning
- Training
- Voice, video and messaging
- Worker guidance
- Worker safety
Device usage and features
Underlying technologies
- AI and data analytics
- Alarming
- BLE & BLE AoA
- Cloud connector
- Connectivity & device O&M
- Data visualization
- Gen AI
- GNSS
- Industrial dataOps
- Industrial protocol adaptation
- Machine and process control
- Mixed reality
- OT network security
- PtX & communications
- Radio link aggregation
- Video analytics and computer vision
- Video processing
- Visual positioning
- Wireless
- Worker sensing
App business values
Industry segments
- (-) Applicable to most industries
- Agriculture
- Airports & Aviation
- Automotive & highways
- Communication Service Provider
- Defense
- Education
- Government
- Healthcare
- Hospitality
- Logistics
- Manufacturing
- (-) Mining
- Oil and Gas
- Public Safety
- Railways
- Renewables
- Seaports & Maritime
- Smart cities
- Systems Integrator
- Utilities
- Webscale
Locations
Device technologies
-
Image

IS540.2 - EX-protected for Europe
Short descriptionIn hazardous environments, such as at chemical plants or in the oil & gas industry, it is crucial to connect workers using purpose-built and certified devices. These must be classified according to ATEX, IECEX, NEC500 or local specifications, EX in short.
IS540.2 by i.safe MOBILE is certified for ATEX zone 2/22 and NEC500 C1D2, and can be used further away from hazardous areas (ATEX Zone 2), where flammable atmosphere is not likely but could occur for a short time.
Manufacturer Manufacturer
Manufacturer
-
Image

IS540.2 - EX-protected for North America
Short descriptionIn hazardous environments, such as at chemical plants or in the oil & gas industry, it is crucial to connect workers using purpose-built and certified devices. These must be classified according to ATEX, IECEX, NEC500 or local specifications, EX in short. IS540.2 by i.safe MOBILE, sold through Exloc in North America, is certified for ATEX zone 2/22 and NEC500 C1D2, and can be used further away from hazardous areas (ATEX Zone 2), where flammable atmosphere is not likely but could occur for a short time.
Manufacturer Manufacturer
Manufacturer
-
Image

IS540 handheld & battery chargers
Short descriptionDesktop charger and Multi charger for phones and spare batteries
Manufacturer Manufacturer
Manufacturer
-
Image

IS540 phone case with belt clip
Short descriptionKeep your phone conveniently fastened in your belt. Tailored for IS540.1 and IS540.2 by i.safe MOBILE.
Nokia Industrial 5G handhelds HHRA501x can also benefit from these accessories.Manufacturer Manufacturer
Manufacturer
-
Image

Litmus Edge
Short descriptionIIoT edge platform
Put data to work for operations to transform at scale. Litmus, the Industrial EdgeOps platform that Unlocks.Activates.Scales. Litmus unifies data collection, normalization, contextualization, and analytics at the edge and cloud. Litmus unlocks intelligence to improve efficiency, profitability and security. Nearly 300 pre-built device drivers and integrations for OT assets and enterprise systems, along with digital twin and machine learning models, make it easier to address asset monitoring, anomaly detection, energy consumption, forecasting, predictive maintenance and more.
Manufacturer Manufacturer
Manufacturer Image
Image
Litmus Edge
Short descriptionIIoT edge platform
Put data to work for operations to transform at scale. Litmus, the Industrial EdgeOps platform that Unlocks.Activates.Scales. Litmus unifies data collection, normalization, contextualization, and analytics at the edge and cloud. Litmus unlocks intelligence to improve efficiency, profitability and security. Nearly 300 pre-built device drivers and integrations for OT assets and enterprise systems, along with digital twin and machine learning models, make it easier to address asset monitoring, anomaly detection, energy consumption, forecasting, predictive maintenance and more.
-
Image

MultiConnect eCell 4G dongle
Short descriptionThe MultiConnect® eCell cellular to Ethernet bridge makes adding cellular connectivity to existing wired assets quick and easy.
Manufacturer Manufacturer
Manufacturer
-
Image

Nozomi Guardian
Short descriptionOT/IIoT asset vulnerability management, threat detection and response
Nozomi Guardian is an operational technology (OT) cybersecurity platform that provides real-time out of band IIoT asset visibility, threat detection and vulnerability identification for critical infrastructure for manufacturing and other industry verticals.
Manufacturer Manufacturer
Manufacturer Image
Image
Nozomi Guardian
Short descriptionOT/IIoT asset vulnerability management, threat detection and response
Nozomi Guardian is an operational technology (OT) cybersecurity platform that provides real-time out of band IIoT asset visibility, threat detection and vulnerability identification for critical infrastructure for manufacturing and other industry verticals.
-
Image

OneLayer
Short descriptionIIoT asset management and zero trust network access
OneLayer manages and classifies IIoT assets helping create inventory. It integrates with CMDB and policy enforcement and acts as a zero-trust access broker enforcing zero trust security principle for IIoT assets. It is directly integrated with FWs for automatic policy enforcement.
Manufacturer Manufacturer
Manufacturer Image
Image
OneLayer
Short descriptionIIoT asset management and zero trust network access
OneLayer manages and classifies IIoT assets helping create inventory. It integrates with CMDB and policy enforcement and acts as a zero-trust access broker enforcing zero trust security principle for IIoT assets. It is directly integrated with FWs for automatic policy enforcement.
-
Image

Palo Alto Networks Next-Gen Firewalls
Short descriptionAdvanced Perimeter Security
Get advanced security powered by Palo Alto Networks. Palo Alto Networks software Next Generation Firewalls use AI and ML to prevent sophisticated cyber threats in the OT environment powered by Nokia MX Industrial Edge (MXIE), without adding physical hardware to the network. The comprehensive solution has industry-leading capabilities such as Advanced Threat Prevention, which blocks unknown command-and-control and exploit attempts in real time, Advanced WildFire, which stops highly evasive malware, DNS Security, which stops emerging DNS based attacks. Additionally, IoT/OT Security quickly profiles all OT, IT and IoT devices and assets, and protects them. This enables advanced security on both the IT and OT sides of the network to protect the entire organization with best-in-class security.
Manufacturer Manufacturer
Manufacturer Image
Image
Palo Alto Networks Next-Gen Firewalls
Short descriptionAdvanced Perimeter Security
Get advanced security powered by Palo Alto Networks. Palo Alto Networks software Next Generation Firewalls use AI and ML to prevent sophisticated cyber threats in the OT environment powered by Nokia MX Industrial Edge (MXIE), without adding physical hardware to the network. The comprehensive solution has industry-leading capabilities such as Advanced Threat Prevention, which blocks unknown command-and-control and exploit attempts in real time, Advanced WildFire, which stops highly evasive malware, DNS Security, which stops emerging DNS based attacks. Additionally, IoT/OT Security quickly profiles all OT, IT and IoT devices and assets, and protects them. This enables advanced security on both the IT and OT sides of the network to protect the entire organization with best-in-class security.
Please complete the form below.
The form is loading, please wait...
Thank you. We have received your inquiry. Please continue browsing.